Preventing malicious activity is a challenge every host faces, but particularly privacy-focused ones. Just as with VPN providers and encrypted messaging apps, a small percentage of users look to use privacy VPS features as a shield against criminal activity.
This kind of activity has always been against BitLaunch's terms of use, and we work diligently, both proactively and reactively, to shut down malicious servers. In the interest of transparency, this blog will outline some of the things we are doing to catch and prevent malicious use of our servers. Note that we may not detail every measure, as doing so may make it easier for malicious users to avoid them.
Malicious activity on BitLaunch: the stats
Due to the diligent work of our abuse team, malicious activity on BitLaunch is rare. Abuse per month accounts for 1% of active servers across all first and third-party hosts.
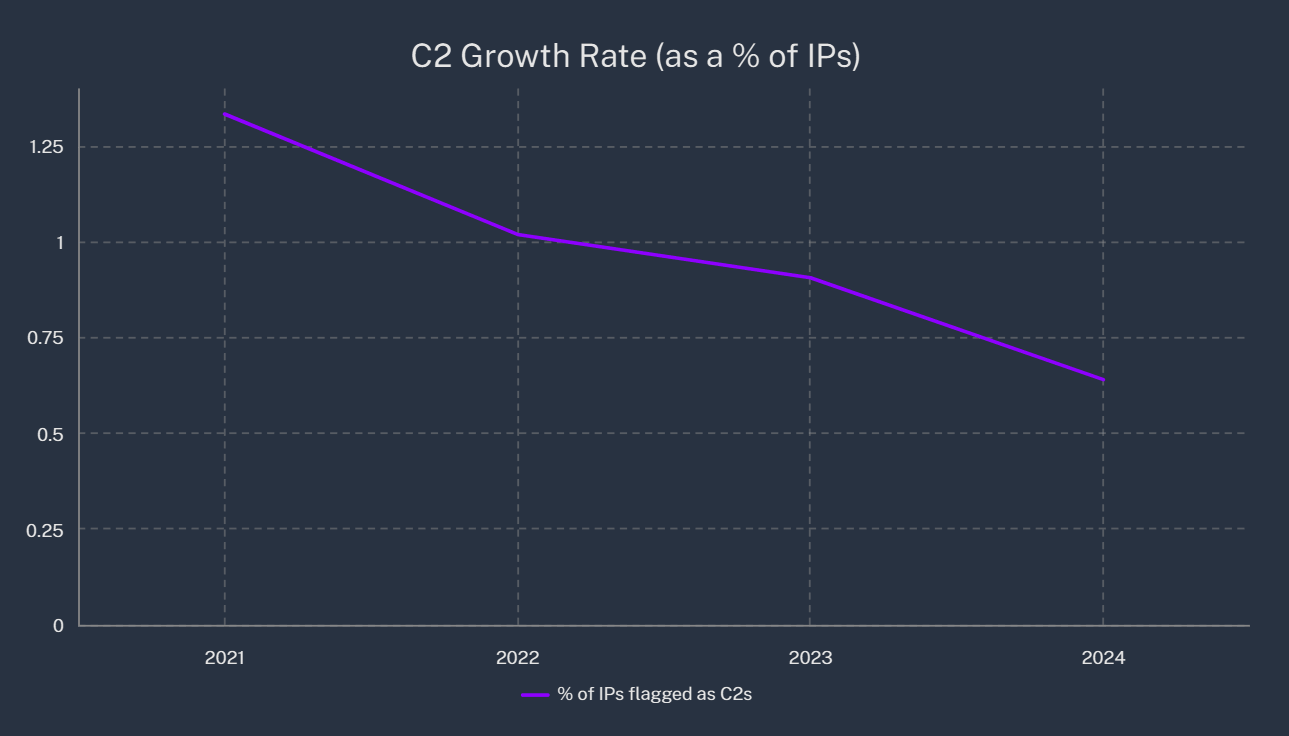
On our first-party servers, BitLaunch naturally has more control and can react quickly to developments. We have been working hard to ensure that the percentage of our IP addresses used as command and control centers (C2s) decreases each year. Since we launched in 2021, this number has dropped by more than half, from 1.33% to 0.64%.
What does BitLaunch consider malicious activity?
BitLaunch considers malicious activity to be any content we believe was intended to cause harm, damage, or loss. This includes, but is not limited to:
- Fraudulent websites or applications designed to cause harm to others (think phishing sites, scams, etc.)
- Servers used to perform Denial of Service (DoS). This type of attack intends to disrupt a target's infrastructure, uptime, or communications by flooding it with illegitimate communication requests.
- Applications designed to cause damage to other systems or perform security violations. This includes using our infrastructure to access any system without permission, as well as probing, scanning, vulnerability testing, or breaching any security or authentication measures. Using our systems to spread malware is naturally also prohibited.
- Unsolicited communication. Sending email-based communications without the recipient's consent is one example of this.
Our third-party partner hosts have their own acceptable use terms, which you must abide by when using their servers. This includes DigitalOcean, Vultr, and Linode.
What isn't malicious activity?
At BitLaunch, we believe privacy and freedom of speech are fundamental rights. As a result, aside from regular hosting activity, we do not consider the following activities to be malicious on our first-party servers:
- Privacy use: hosting VPNs and proxies, as well as privacy-focused cloud storage, chat, and search engine apps.
- Hosting Tor exit nodes: You can run Tor Exit, Relay, and Bridge nodes on BitLaunch servers. Just let us know if you are running an Exit node so that we can deal with abuse complaints. Naturally, we will not accept purposefully malicious activities.
- Free speech: We support free speech on our platforms, so long as it does not constitute hate speech or encourage violence.
Note that we cannot guarantee that our partner hosts will have the same philosophy. You should check their acceptable use terms to determine where you want to launch your server.
How does BitLaunch stop malicious activity?
BitLaunch employs a full-time, dedicated abuse team that works both proactively and reactively to stop malicious activity on our platforms. They use a variety of industry-standard tools to do so, including (but not limited to):
- Abuse.ch: Helps us to identify, track, and stop malicious activity originating from our servers.
- Urlscan.io: A free tool that scans and analyzes websites for malicious content and allows users to submit reports.
- Spamhaus: A tool to help detect, block, and prevent spam and malicious emails, including proactively defending against emerging threats. We use Spamhaus's reputation manager to check for issues.
- Elliptic: Provides blockchain analytics services to ensure that we do not accept cryptocurrency payments from known illicit sources and wallets associated with criminal activity.
Sometimes, BitLaunch must take more drastic action. This includes no longer serving certain regions where a high percentage of abuse originates. We, of course, also act when harmful content is reported to us directly, whether that is from security researchers, law enforcement, or regular internet users.
Actions we take when malicious activity is suspected
Upon report of abuse, the offending server is usually quickly taken offline and suspended. After investigation, a member of the support team informs the user of the offense and provides them with simple resolution instructions. Failure to address abuse reports can lead to account termination.
In severe cases, we destroy the server to prevent further damage and permanently ban the account responsible, with no chance to appeal.
Why we're writing this post
Privacy-focused services are painted as shady and unscrupulous, with (usually unfounded) accusations that they are not doing enough to prevent cybercrime. This is especially true when they accept payments in cryptocurrency like BitLaunch does or use end-to-end encryption. We want to help dispel this myth.
Organized criminals don't need private services to remain anonymous. According to some sources, $3.2 trillion of fiat cash is implicated in criminal activity annually versus just $20 billion in cryptocurrency. Criminals can purchase fake and stolen identities for pennies. They can also pose as legitimate companies, use sophisticated money laundering schemes, etc. By being transparent about what we do to prevent abuse on our platform and the statistics surrounding it, we hope to highlight that private services are used far more for good than they are for evil.
You can read our acceptable use policy in full here. If you have further questions about how BitLaunch deals with malicious activity, please reach out to our support team.
