Virtual Private Networks (VPNs) have experienced explosive growth over the past decade. Once a tool used almost exclusively by businesses, they have managed to capture the market and mind share of the general public. According to some resarch, the global industry could be worth up to $151 billion by 2030, driven by growth in the US and Asia.
But what exactly are VPNs? What are they used for, and what should you look for when buying one? We’ll be answering that in this guide, covering:
- What is a VPN and how does it work?
- What are VPNs used for?
- Is my VPN secure?
- What should you look for when buying a VPN?
- The overlooked aspect of VPN privacy
- Creating private VPNs with BitLaunch
What is a VPN and how does it work?
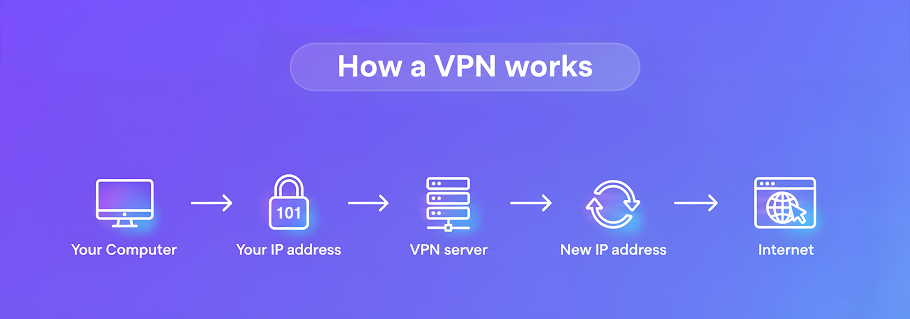
A virtual private network (VPN) is a tool that secures the connection between your device and another computer (or server) over the internet. This is usually achieved by encrypting your traffic before it leaves your computer and routing it through a remote server, usually controlled by your VPN provider.
Browsing the internet in this way has two core benefits:
- As your traffic is scrambled using strong encryption, it prevents an attacker from intercepting your web activity and either snooping or using a man-in-the-middle (MiTM) attack to redirect you to their own malicious website.
- A VPN masks both your IP address and the websites you are visiting from others. This prevents your internet service provider (ISP) from keeping an accurate record of the websites you have visited, while making it harder for analytics companies to track you across the internet.
There are, however, some drawbacks. The process of encrypting and re-routing your traffic slows down your connection. Using some VPN services also leads to more CAPTCHA challenges, with some websites block known VPN IP addresses from accessing their site entirely.
What is a VPN client or VPN app?
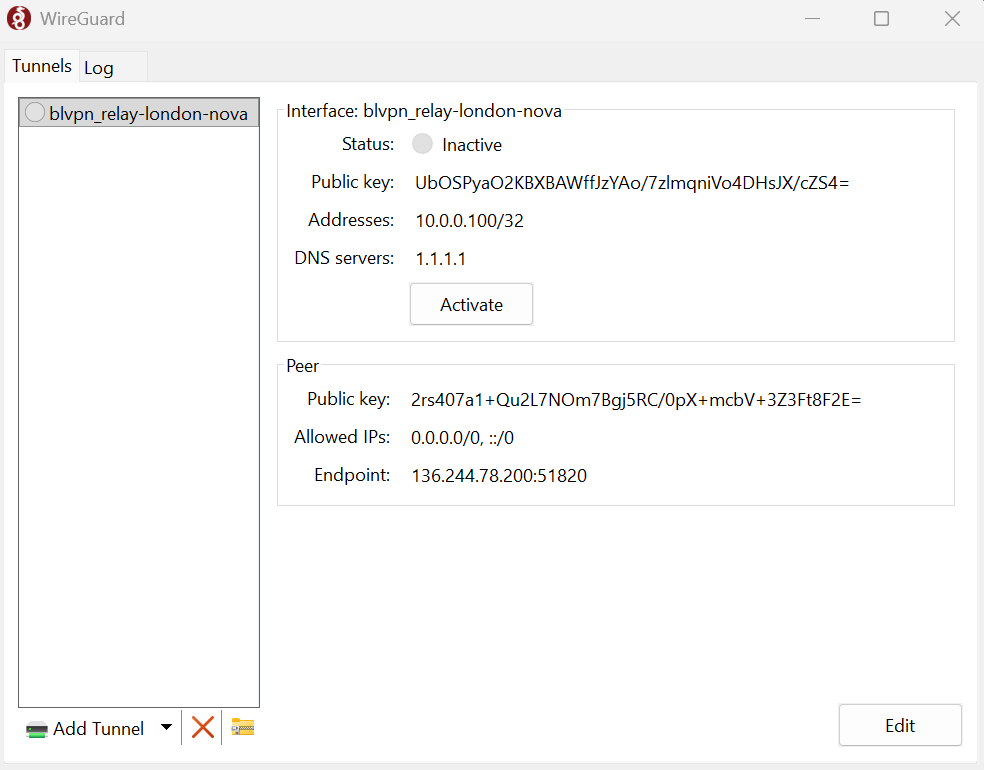
Modern VPNs require users to download a VPN client or VPN app to use them. This allows users to select the server they want to use, as well as log in to their account and enable or disable certain features.
Most VPN providers have their own VPN client, but there are open source ones, too. The most popular are WireGuard and OpenVPN.
What is a VPN kill switch?
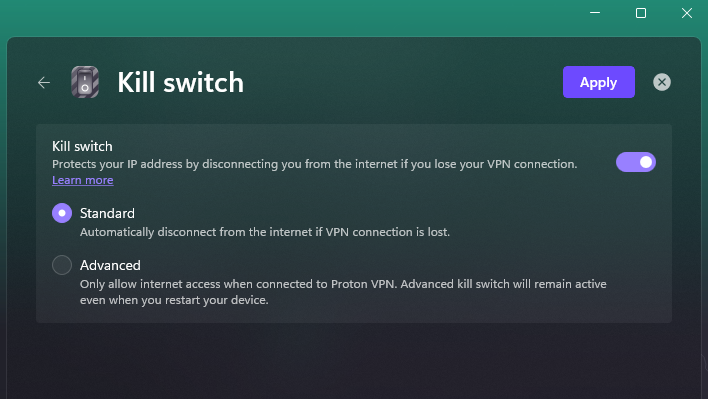
Usually, when a VPN connection fails, your device falls back to your regular internet connection. This can temporarily leak your real IP address to the services you're using and the websites you are visiting to your ISP.
A VPN kill switch acts as a safety mechanism. It disables your internet when the VPN connection fails, preventing traffic not protected by it from reaching the internet or your ISP.
What are VPNs used for?

Despite a few downsides, having access to a VPN can be incredibly useful. While there are dozens of use cases, the primary ones include:
Protecting users on public Wi-Fi
These days, almost all websites support SSL (HTTPS), which means your traffic on public networks is usually encrypted and largely safe. However, there are still some attacks, such as SSL stripping, and win access points that can pose a threat.
Additionally, an attacker or network admin can usually see which HTTPS websites you are visiting, even if they can’t see the specific webpages or traffic. A VPN makes it much more difficult to perform these attacks and prevents users from being able to see which websites or services you’re connecting to.
Protection against IP tracking
Websites often run trackers. If you visit two websites that use the same tracking service, the advertiser can often use your IP address to identify and correlate your traffic. This allows companies to direct targeted advertising your way based on information that you did not knowingly provide them.
As routing your traffic through a VPN changes your IP address, it can limit the amount of quality data analytics and advertising companies can collect about you. All they will see is the VPN IP address, which could be shared with other users.
Keep in mind that a VPN does not stop other kinds of tracking. If you sign into a site or app, they’ll still know it's you. Advertisers can also use techniques such as browser fingerprinting and payment processor information to track you even if you’re using a VPN.
Privacy from your ISP (and throttling prevention)
By default, your internet service provider (ISP) can see and log every domain you visit. This is necessary to provide DNS services. Unfortunately, many also use it for ill. Some may sell the data to advertisers, censor content, throttle connections to some sites, or provide it to law enforcement. A VPN tunnels and encrypts your DNS requests as well as your traffic, which prevents this kind of tracking and throttling.
Staying private while torrenting
Some ISPs throttle download speeds while torrenting because they assume that all peer-to-peer traffic is piracy. A VPN encrypts torrent traffic – an ISP can't tell what you're doing, only that you are using a VPN.
VPNs also aid privacy while torrenting. Copyright holders sometimes spy on torrent to gather IP addresses. They then pass this information to the ISP, who sends the user an informal copyright notice with threats of legal repercussions if they do not desist. As VPNs change your IP address, they make this process much harder.
Accessing streaming catalogs from other countries
Rather than buy global rights to stream movie or TV content, streaming services such as Netflix often buy the rights to show content in specific countries. This makes logical sense – why buy the rights to show a Chinese drama in every country when it will only be watched in Asia? Unfortunately, as streaming providers become more and more obsessed with maximizing every penny of their licensing budget, streaming catalogs have become fractured and unintuitive. You’ll see behavior such as Dune Part 2 being available in the UK, but Part 1 only in French Polynesia.
VPNs allow you to route your traffic through a country of your choice. This gives the streaming provider the impression you’re connecting from somewhere else, and therefore must deliver that nation’s streaming catalog instead. This can greatly increase the number of titles available on any given streaming platform and allow users to get more out of their subscription.
Bypassing censorship
A government or ISP will find it difficult to stop you from visiting a website if they don’t know what website you’re connecting to. Because VPNs obscure your traffic, they’re an effective way to circumvent censorship or avoid age gates. That said, you should also keep in mind that your ISP can still see that encrypted VPN traffic is leaving your device and block it. As a result, proxies are sometimes more effective for this purpose.
Online gaming
Online games often block IP addresses to prevent users from simply creating a new account when they get banned. A VPN can change your IP address and, therefore, allow you to bypass these blocks as well as prevent your IP from leaking to other players.
VPNs can also result in lower latency when gaming if there are problems along the default route your packets travel, your ISP routes your traffic poorly, or a competitor is performing a DDoS attack. In most instances, however, using a VPN for gaming will only increase latency due to the additional overhead of encryption and re-routing.
Protecting smart home (IoT) devices
Smart home devices are increasingly commonplace, but not all of them are secure. Cheap or outdated devices can inadvertently leak private information such as which devices you have or when you’re home to attackers. Activating a VPN on your router ensures that all traffic passes through a single secure connection, preventing outsiders from interpreting it or targeting devices via their IP address.
Finding better deals for flights, hotels, car rentals, and more
Retailers and online booking sites sometimes show different prices in different regions, charging more where the demand is highest. They may also log your IP to see how many times you have visited a site and manipulate prices based on that.
VPNs allow you to identify and sometimes bypass such practices by letting you compare prices from multiple virtual locations.
Corporate VPNs for remote work
Corporate VPNs are usually set up by a company to allow its employees to access content that is restricted to its internal network without compromising security. They can browse as if they are in the office, with all of the access but also all of the restrictions that come along with that.
Is my VPN secure?
Despite what providers will have you believe, buying a VPN doesn't automatically equal better security online. A VPN with poor server security or configuration may leak your information and leave you more vulnerable than before.
Choosing trusted brands is a good start, as is checking for independent, third-party audits of their security. Beyond that, you should be considering if the protocols and features your VPN offers are fit for purpose and that the VPN does not have basic issues such as DNS leaks.
VPNs and protocol types
Not all VPNs are suited to every purpose, and the protocol used can play a major role in that. The protocol affects security, speed, versatility, configuration difficulty, and beyond. There are six main protocols used by VPN providers today, which we'll cover in order of their current popularity.
WireGuard
The most common protocol in modern VPNs is WireGuard. It quickly gained popularity for its ability to combine lightning-fast speeds and strong cryptography while being simple to configure and having a small codebase to audit.
WireGuard is all about efficiency, agility, and security. However, this comes with some tradeoffs. WireGuard is vulnerable to deep packet inspection on controlled networks if the VPN provider does not implement additional layers of obfuscation. WireGuard also operates exclusively over UDP by default. This allows for better performance, but is more likely to be blocked by firewalls on controlled networks.

OpenVPN
OpenVPN is a little slower than WireGuard, both in terms of speed and connection time. It is far from obsolete, however. OpenVPN can run over either TCP on port 433 or UDP, depending on whether a user wants to prioritize speed or blend in with regular HTTP traffic on restricted networks. It is also more obfuscated than WireGuard by default, and there's generally less risk of metadata being left behind on the server. This, along with its maturity, makes it particularly suitable for the enterprise.
IKEv2/IPSec
IKEv2 and IPSec are two technologies commonly combined to provide a fast and stable VPN experience. Together, they provide adequate security, though it is worth noting that leaked NSA presentations suggest that US intelligence has found a way to decrypt some communications encrypted using IPSec and IKE. IKEv2 is also closed source, which may be a concern for some.
The main advantage of using IKEv2/IPSec over OpenVPN or WireGuard is its compatibility. Unlike the other two, it does not require any additional software to use because support is built into most operating systems. IKEv2 also reconnects automatically and is faster than OpenVPN, though it is more complex to configure and more likely to be blocked on restricted networks, as it does not support TCP.
SSTP
The Secure Socket Tunneling Protocol (SSTP) is a cryptographically secure VPN protocol that transports Point-to-Point Protocol (PPP) traffic through an SSL/TLS channel. Its primary advantage is its stealth: SSTP uses the same port as regular encrypted browsing traffic, and the same protocol (SSL). In other words, it's practically indistinguishable from regular traffic, which is a huge advantage if you don't want your ISP, government, or network admin to know you're using a VPN.
Compared to modern UDP-based VPN protocols, SSTP is relatively slow, and it's also proprietary. The lack of transparency may be a concern to those who are worried about hidden backdoors or undisclosed vulnerabilities.
L2TP/IPsec
IPSec can also be combined with L2TP, but this is generally considered a legacy configuration. You won't find it in many VPNs, and if you see it as the only option, the VPN is very outdated.
While simple and built into many older operating systems, it's relatively slow and easy to block. If configured correctly, L2TP/IPsec can provide acceptable security and privacy, but misconfiguration is not uncommon due to its legacy nature. This can lead to major vulnerabilities, and for this reason, many VPN providers no longer use it. Ultimately, there are better options for the average consumer; however, it has some staying power in the enterprise, where a trusted IP administrator can oversee its setup.
PPTP
PPTP is a basic, legacy VPN protocol that has major security vulnerabilities. While it is the fastest of all protocols, this is because it uses weaker encryption, which has less overhead. PTTP is also easy to block, not particularly reliable, and runs into compatibility issues with some routers. A VPN provider still using PPTP in the current year should be seen as a red flag.
What is a DNS leak, and how do you stop them?
A DNS leak is when your ISP's domain name service is being used to resolve URLs, despite you being connected to a VPN. A DNS service is what converts the address you enter into your URL bar into a series of numbers that a computer can understand, and vice versa.

Preventing your DNS from leaking is important if you want privacy from your ISP. They often store a list of DNS lookups associated with your IP address, which essentially means a log of every website you visit (but not specific pages). In some countries (such as the UK), ISPs must keep this data to hand for a certain number of years so that law enforcement can compel them to hand over their records if necessary.
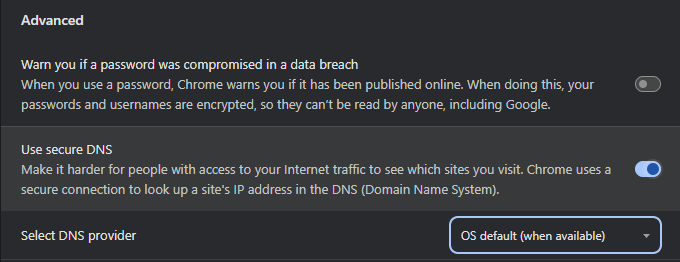
How can I stop DNS leaks?
The most common reason for DNS leaks when using a VPN is browser configuration. The first thing to try is turning off "Secure DNS" in your browser settings. This is usually found in Settings > Privacy & Security > Use/Enable Secure DNS.
After performing this change, check for DNS leaks again. If you still see your original IP address, there are several other changes you can try:
- Ensure any "DNS leak prevention" features are enabled in your VPN settings.
- Flush your DNS cache with `
ipconfig /flushdns` in command prompt. - Check your anti-virus software for website shields that block fake and scam sites. These often hijack your DNS.
- If you're using Firefox, you may need to disable DNS over HTTPS, a default in some countries which uses Cloudflare to encrypt your DNS traffic.
- If you're on Windows 11, you may also need to disable DNS over HTTPS if you have previously set a custom DNS.
- Check for browser extensions that change your DNS. Some examples are proxy and web safety plugins.
- Run a malware scan. There's a small chance that a malware infection is modifying your DNS.
If none of this works, the problem may be a misconfiguration on the part of your VPN provider, particularly if it's a free one. If possible, reach out to their support team for further assistance. BitLaunch VPN customer? You have access to around-the-clock expert support — don't be afraid to reach out!
What should you look for in a VPN?
The VPN industry is full of dubious claims, misleading marketing, and undisclosed sponsorships. It can be really difficult to know which VPN features are actually important and which are snake oil designed to make you feel like you’re getting value. The way we see it, there are four core features you should not neglect, and several other situational “nice to haves”.
- No log policy (preferably independently verified)
- Killswitch
- Modern protocols
That's all well and good, but what do these features actually mean and why are they important?
What is a no-log VPN?
A no-log VPN does not keep records of its users' internet activity. True no-log VPNs will not track which websites customers visit, the times they're using the VPN, how much data they transfer in a session, or their IP addresses. This is distinct from VPN providers that collect such data but claim to anonymize it.
If you are buying a VPN for privacy, a provider that doesn't keep logs is crucial. A VPN provider that logs may provide them to law enforcement, advertisers, partners, and more. Often, a VPN with logs is more privacy-invasive than a customer's ISP, since the businesses are typically based in regions with less regulation.
How do you verify that a VPN provider doesn't log?
Most VPN providers claim to have "no-log" policies in their marketing materials, but words are cheap. As a consumer, you must have trust that your provider a) isn't lying and b) isn't negligent in this regard.
First off, yes, it would be business suicide for a VPN provider to claim it keeps no logs and then get caught out. Unfortunately, that doesn't always stop them. There is no way to know with 100% certainty that a provider is not logging. This is why we recommend setting up your own. These days, it's quick and easy to set up a VPN on a VPS and ensure logs aren't being stored on your server.
That said, there are a few things you can look for to increase your trust in a provider's no-log policy:
- Independent audits: Regular, third-party audits that specifically examine logging practices are an effective way to demonstrate a commitment to a no-log policy. Ensure you read the report directly, rather than relying on the VPN provider's word for it. Their summary of the audit may be misleading.
- Court cases and subpoena responses: If an entity has successfully and legally compelled a VPN provider to hand over its logs, but it was unable to, it's a good sign.
- Jurisdiction: It's better if your VPN provider is located in a country where there is no pressure for them to keep logs, surveil users, or implement government backdoors. However, keep in mind that a provider being outside of the "Five Eyes" isn't all it's cracked up to be. They can still cooperate with law enforcement. There's even a point to be made that offshore companies are more removed from liability and therefore more likely to take risks.
- Technical design details: Look for clear explanations of how a provider avoids data seizure and logs. Key details include full disk encryption, RAM-only (volatile) storage, and how authentication is decoupled from activity logs.
Free VPNs — are they worth it?
We tested several free VPNs and found the same outcome: increased blocking and slower speeds. Out of hundreds of VPNs, two offer an acceptable free service: Proton and Windscribe. Windscribe limits you to just 2 GB of free data, whereas Proton does not allow you to freely select your country. Instead, the server location is chosen randomly from a pool of six countries. Speeds are also quite slow at just 32 Mbit.
But the bigger question with free VPNs is perhaps not what you're getting, but what you're giving away. Free VPNs have one of three purposes in mind: harvesting your data, spreading malware, or converting you into a paying customer. All of these outcomes are likely to end poorly for the end user.
The overlooked aspect of VPN privacy
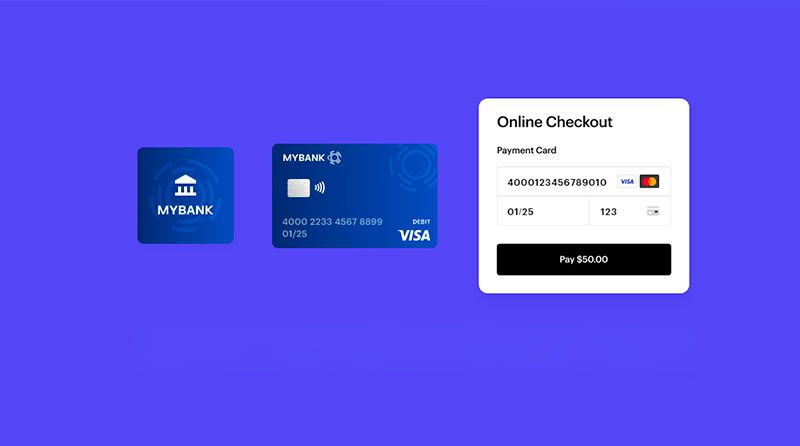
So far, we've focused a lot on the technical aspects of VPN: what they are, how they work, how to secure them, and the protocols used. But there's another, more fundamental aspect to VPN privacy — how you pay for them.
With all of the focus on server speeds, logs, jurisdictions, and DNS records, it's easy to forget that you leak your true identity every time you enter your card details. When you pay with a credit or debit card, some details will always be shared with the merchant for fraud prevention purposes. This includes your full name, address, CCV, and other details. This information is often stored for some time, and frequently passed on to third-party payment providers or other partners.
A VPN provider knowing your true identity does not automatically compromise your browsing privacy. It does, however, require you to place a lot of trust in your VPN provider. If they don't follow good practices and keep no logs or metadata, you could be de-anonymised in the case of a leak or law enforcement request/raid.
For these reasons, buying a VPN with cryptocurrency is a smart additional step.. Because cryptocurrencies are less regulated than fiat currency, providers don't need to ask for your name or address. Usually, an email address is the only requirement, and this can be a temporary or throwaway mail.
That said, most VPNs don't accept cryptocurrency. Many that do use third-party payment providers such as CoinGate to do so, which is not ideal. The fewer parties your information is shared with, the better.
Private VPNs with BitLaunch
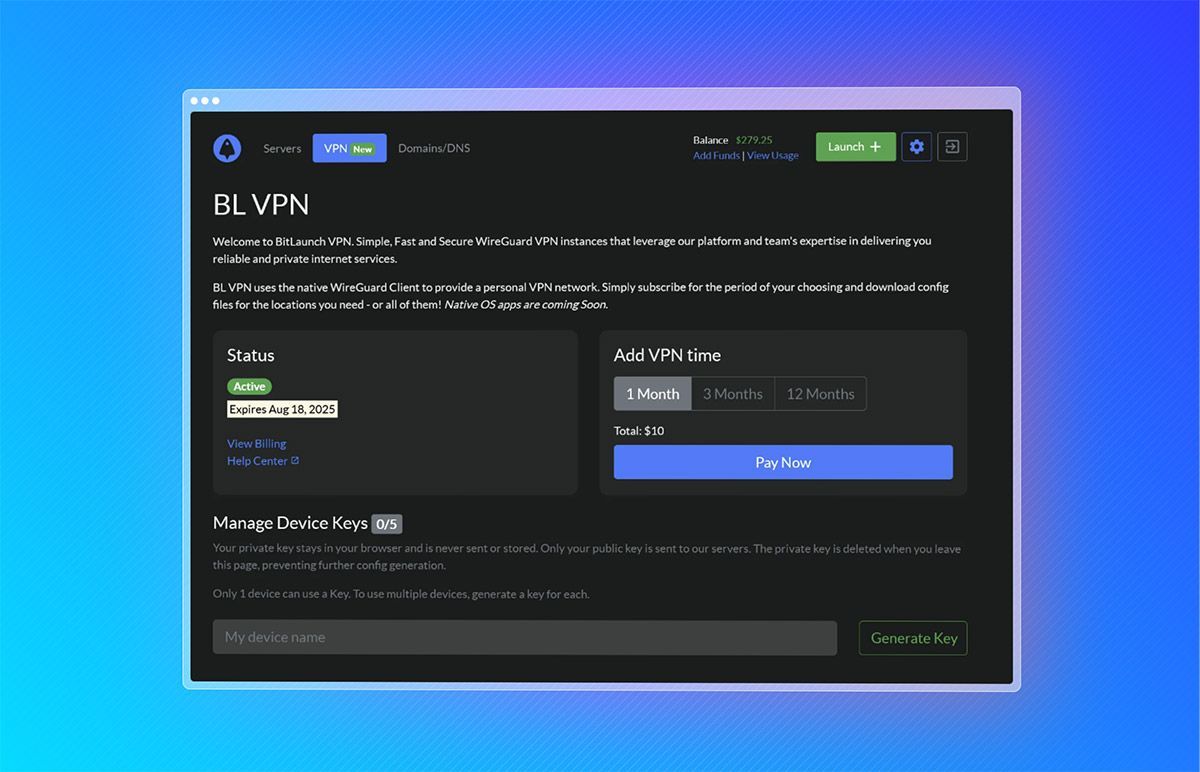
BitLaunch takes payment privacy a step further. We built an in-house cryptocurrency payment system with privacy at its core. We don't share your with third parties and don't need to charge extra to cover the fees those third parties take. All of this builds on our long-term commitment to privacy. No logs, no trackers, no analytics, and the ability to destroy your data at any time.
Still don't trust our first-party VPN? We let you build your own. Utilize our high-speed anonymous VPS infrastructure and one-click apps to launch your own VPN in minutes. You get full control over your server, including the ability to add additional security and ensure there are no logs stored.
New users can sign up to BitLaunch and talk to our support for some free credit. Get started with a private, fast, and secure VPN today.